Your Organization will use a TVTools booking solution to display the calendar of some of your Office365 resources
To access your data TVTools uses EWS access authorized by an Azure application, with the following rights
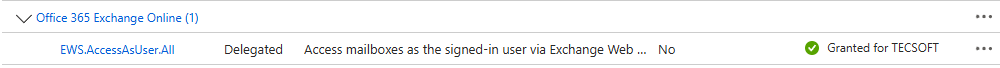
The method currently used requires impersonation rights to access your calendars.
This method will no longer be functional from February (exact date unknown)
https://techcommunity.microsoft.com/blog/exchange/critical-update-applicationimpersonation-rbac-role-deprecation-in-exchange-onlin/4295762
We must change the delegated right “EWS.AccessAsUser.All” to the application right EWS.AccessAsApp
This last right gives exorbitant privileges to the application, and it is not recommended to assign it globally to the application (which would obtain all the control over your Exchange)
In order to give this right only to the necessary resources, and following Microsoft’s recommendations, it is necessary to set up an RBAC strategy,
as indicated in the link above:
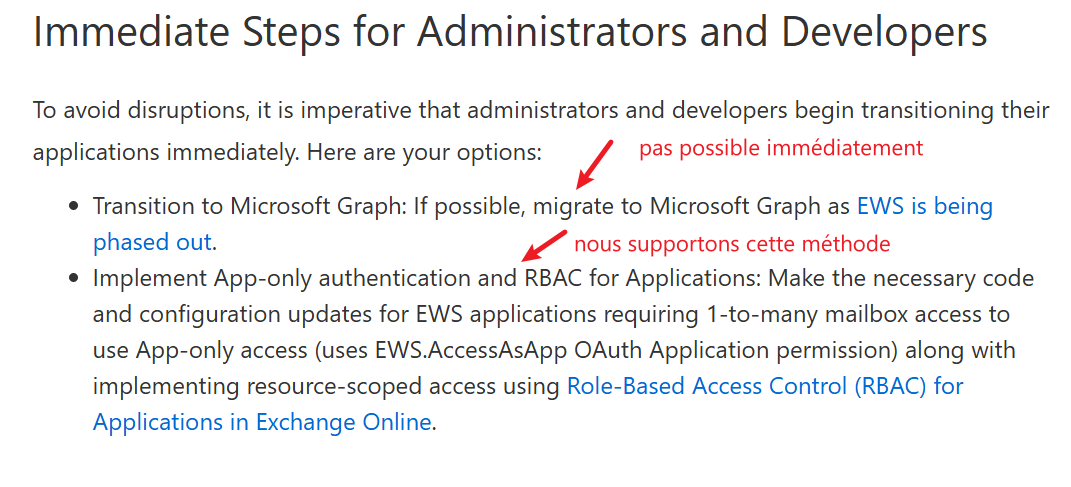
For information on RBAC:
https://learn.microsoft.com/en-us/azure/role-based-access-control/overview
For an example of deployment:
https://learn.microsoft.com/en-us/exchange/permissions-exo/application-rbac
English tutorial explaining the procedure
https://practical365.com/migrate-from-ews-application-access-policy-to-rbac-for-applications/
Procedure
Goal: assign an EWS.AccessAsApp application role to the Azure application “TVTools Calendars” for members of the Azure group “TVTools Group” then, you just need to put the rooms in the “TVTools Group” group for the TVTools Booking application to work
- Put the resources (rooms) to which TVTools must have access in an Azure group: in the following this group will be called for example “TVTools Group”
(why do it at the beginning: the propagation time of RBAC modifications: 2h… so if you want to do immediate tests, the rooms must already be members of the group)
à this has been already done by Prasad. - Create a new Microsoft Entra ID application, let’s call it: “TVTools Calendars”
(no other configuration, no platform to add)
Create a secret, keep its value
please remove “User.read” right and add the application right “User.Read.all”

please note Client ID, Tenant ID and Secret Value and send these datas to Tecsoft
The next phase should be done by a global admin in a powershell window or powershell ISE
if you are not familiar with powershell and Microsoft Graph, please install the 7.5 or above version of powershell
and enter:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
Install-Module -Name ExchangeOnlineManagement
Install-Module Microsoft.Graph -Scope CurrentUser -Repository PSGallery -Force
Install-Module Microsoft.Graph.Users -Scope CurrentUser -Repository PSGallery -Force
Install-Module Microsoft.Graph.Authentication -Scope CurrentUser -Repository PSGallery -Force
Connect-ExchangeOnline
Connect-MgGraph -Scopes ‘Application.Read.All’
(the install can take several minutes)
- Creation of a ServicePrincipal for the Entra Id application “TVTools Calendars”
$SP = Get-MgServicePrincipal -All
$ServicePrincipalId = $SP | Where-Object {$_.displayName -eq “TVTools Calendars”} | Select-Object -ExpandProperty Id
$AppId = $SP | Where-Object {$_.displayName -eq “TVTools Calendars”} | Select-Object -ExpandProperty AppId
Write-Host (“AppId is {0} and Service Principal Id is {1}” -f $AppId, $ServicePrincipalId)
New-ServicePrincipal -AppId $AppId -ServiceId $ServicePrincipalId -DisplayName ‘PS RBAC TVTools Calendars’
To verify
Get-ServicePrincipal | ? AppId -EQ $AppId | fl
Should return no error and verify that the AppId is not null or empty
if null
please try
$SP=Get-MgServicePrincipal -ConsistencyLevel eventual -Count spCount -Filter “startsWith(DisplayName, ‘TVTools Calendars’)”
$SP
if $SP if well defined please continue with
$ServicePrincipalId = $SP | Where-Object {$_.displayName -eq “TVTools Calendars”} | Select-Object -ExpandProperty Id
$AppId = $SP | Where-Object {$_.displayName -eq “TVTools Calendars”} | Select-Object -ExpandProperty AppId
Write-Host (“AppId is {0} and Service Principal Id is {1}” -f $AppId, $ServicePrincipalId)
And verify that
Get-ServicePrincipal | ? AppId -EQ $AppId | fl
Should return no error and a valid AppId
- creation of a “scope” for the “TVTools Group” group
$scopedGroup = Get-Group ‘TVTools Group’
New-ManagementScope “TVTools Scope” -RecipientRestrictionFilter “MemberOfGroup -eq ‘$($scopedGroup.DistinguishedName)'”
To verify
Get-ManagementScope “TVTools Scope” | fl
Should return no error
5. Assignment of an “EWS.AccessAsApp” role to the scope
New-ManagementRoleAssignment -App $AppId -CustomResourceScope ‘TVTools Scope’ -Role ‘Application EWS.AccessAsApp’
New-ManagementRoleAssignment -App $AppId -CustomResourceScope ‘TVTools Scope’ -Role ‘Application Calendars.ReadWrite’
To verify
Get-ManagementRoleAssignment -Role ‘Application EWS.AccessAsApp’ | fl
Get-ManagementRoleAssignment -Role ‘Application Calendars.ReadWrite’ | fl
Should return no error
- check the operation:
Test-ServicePrincipalAuthorization -Identity $AppId -Resource delta@tvtools.info
à must be OK if delta@tvtools.info is member of “TVTools Group”
Test-ServicePrincipalAuthorization -Identity $AppId -Resource omega@tvtools.info
à must not be OK if omega@tvtools.info is not member of “TVTools Group”
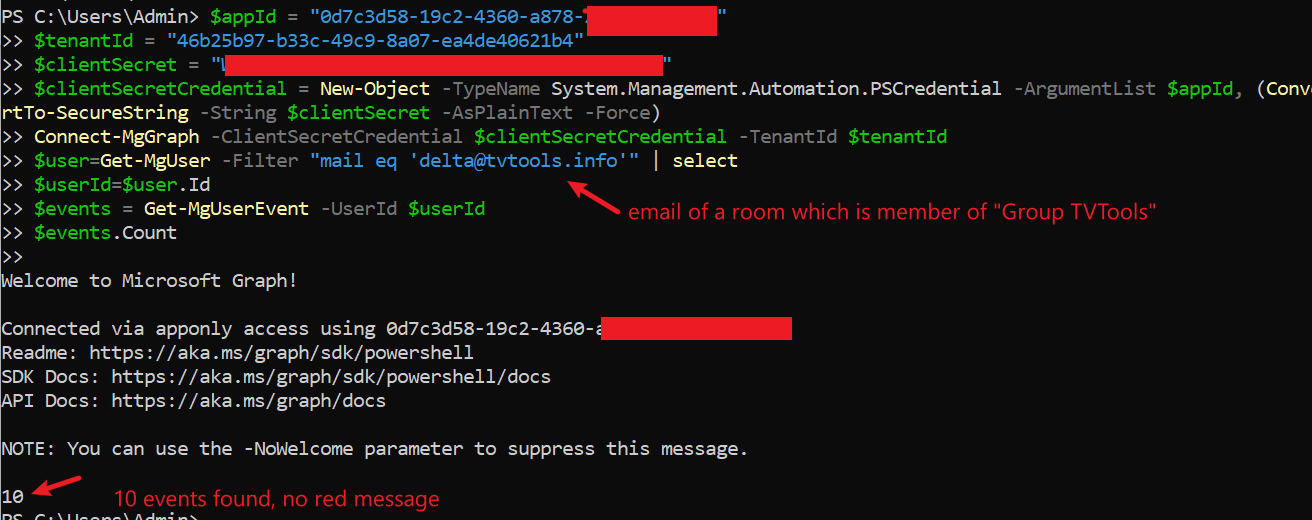
- confirmation of operation: retrieval of events from a room calendar delta@tvtools.info (please change to one of your ressources)
$appId = “xxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx put the client Id of your application Entra Id”
$clientSecret = “put the value of the secret of your application”
$tenantId = “put the tenant of your organization”
$clientSecretCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $appId, (ConvertTo-SecureString -String $clientSecret -AsPlainText -Force)
Connect-MgGraph -ClientSecretCredential $clientSecretCredential -TenantId $tenantId
$user=Get-MgUser -Filter “mail eq ‘delta@tvtools.info'” | select
$userId=$user.Id
$events = Get-MgUserEvent -UserId $userId
$events.Count
example result for a room delta@tvtools.info which is a member of the group “TVTools Group”
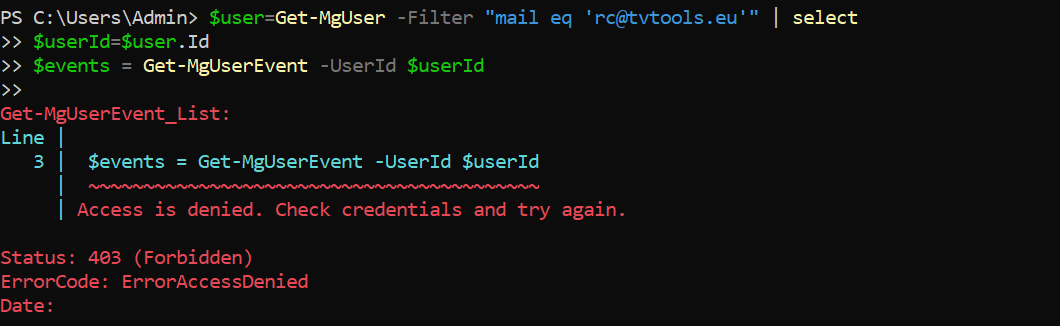
example result for an rc@tvtools.eu account that is not a member of the “TVTools Group” group
- Please send to Tecsoft, the Client Id, secret Value and Tenant Id of your Microsoft Application ID, once this procedure is validated.
Note: the modifications that you make to your main service, scope, role, member of the group “TVTools Group”, can only be taken into account after 2 hours… it is very penalizing for the tests….
https://learn.microsoft.com/en-us/exchange/permissions-exo/application-rbac


